Florian Pester · 2 min read
Securing Legacy Software Applications
Outdated legacy systems lack maintenance, support for modern encryption algorithms, and compatibility with current security software. KronoCore is designed to address these issues, ensuring your legacy applications run reliably and securely. Instead of expensive and risky redesign, KronoCore extends the lifetime of useful software indefinitely.

Outdated legacy systems lack maintenance, support for modern encryption algorithms, and compatibility with current security software. KronoCore is designed to address these issues, ensuring your legacy applications run reliably and securely. Instead of expensive and risky redesign, KronoCore extends the lifetime of useful software indefinitely.
KronoCore creates an isolation layer around legacy application servers and legacy client components. This isolation helps prevent unauthorized access and protects against known vulnerabilities. Secure communication paths are established, allowing continued use of legacy web-based applications — even those written in venerable technologies such as Flash or similar unmaintained technology — through modern, compliant channels.
KronoCore offers:
- Isolation of legacy systems to reduce security risks.
- Secure communication channels that utilize state-of-the-art encryption.
- Tightly monitored and controlled access to prevent exploitation of vulnerabilities.
- Integration with existing corporate infrastructure through virtualization.
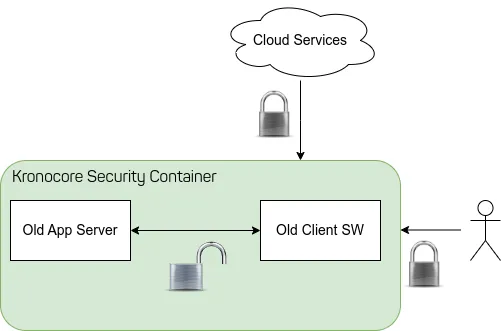
Consider the image above. KronoCore isolates a legacy application and a legacy client software from the rest of the infrastructure so that the organization is compliant and secure. To provide efficient access to users KronoCore offers a secure channel for the rest of the infrastructure (such as any Cloud Applications) and human users.
Since KronoCore is updated independently from any legacy software it always provides state-of-the-art security and encryption to its secure communication channels. Because the legacy systems are virtualized they are easy to integrate into existing corporate infrastructure, cluster management systems, or private cloud setups.
KronoCore provides access to legacy systems only via secured, tightly monitored, and hardened communication paths, making it impossible for an attacker to gain enough access to exploit vulnerabilities. We are continuously working on further hardening legacy systems, including active defense mechanisms — such as intrusion detection, real-time monitoring, and automated threat response. These mechanisms are specifically designed to protect legacy systems from known exploits and attacks.
If your organization is facing challenges with legacy software, contact us! We are eager to help securely integrate legacy applications into the modern IT landscape and transform your legacy systems’ security and compliance.