Florian Pester · 3 min read
The case for legacy software
Physical Infrastructure in the real-world has a much longer lifetime than software systems. This presents a number of challenges to operators: Hardware components fail at some point while spare parts are no longer available and need to be replaced by modern alternatives. Old software lacks support for modern components and a major software upgrade is required for continuing operation. Learn how this gap can be mediated and what can be done to solve this issue long-term.
Most of the infrastructure in our world is planned with decades of planning horizons. Streets, bridges, rails are all planned for at least 40 years of use, often more. The average age of electrical power plants is about 60 years in most developed countries. Railway infrastructure in most European countries has a similar age.
In software things are dramatically different. Your typical software system is supported for 5 - 10 years, maybe 15, if things go really great. The Long Term Support of the Linux kernel lasts for 3 years — an order of magnitude less than your typical real world infrastructure. This situation creates a great number of challenges for the teams maintaining real world infrastructure, such as:
- It can become increasingly difficult to find replacement hardware.
- Cyber-Security becomes a nightmare.
- Maintenance, management and embedding legacy solutions into an evolving ecosystem presents increasing challenges or becomes downright impossible
When you operate a great number of computers, encountering hardware failures is to be expected and only a matter of time. If your software is too old, it will not “just run” on newer hardware. This presents a challenge to your supply chain.
Windows 7 is not supported on hardware released after 2015. Windows 10 has no official date yet, but it is foreseeable that it will run into the same issue. Windows 10 is also the last version of Windows to support 32-bit hardware, which presents another challenge when considering an upgrade to Windows 11. In the Linux world the situation is slightly better, but if your Linux system is older than 10 years you will almost certainly have problems with modern hardware.
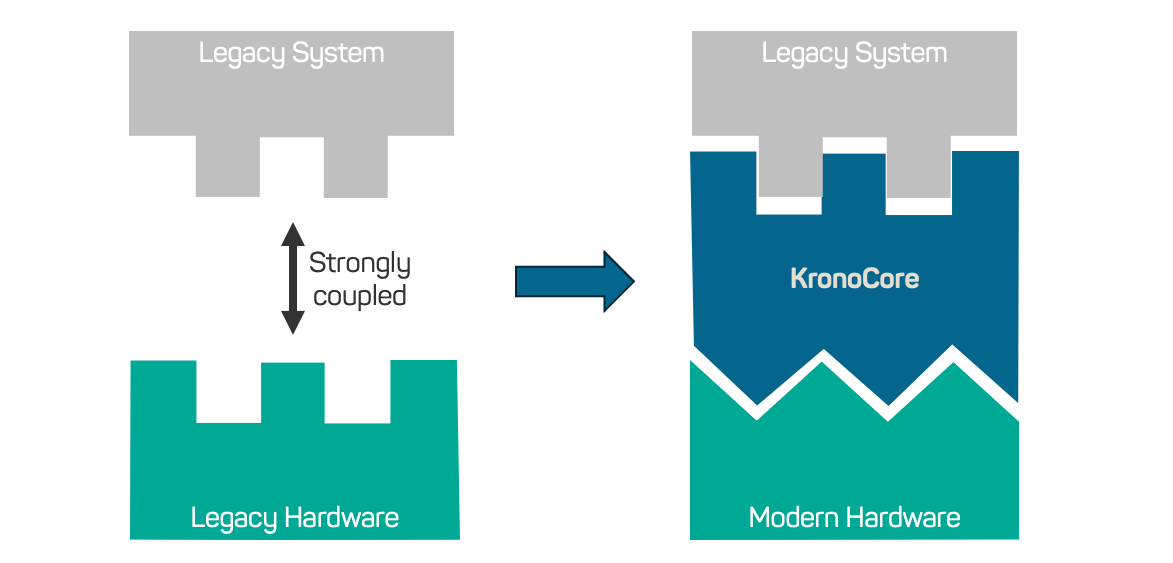
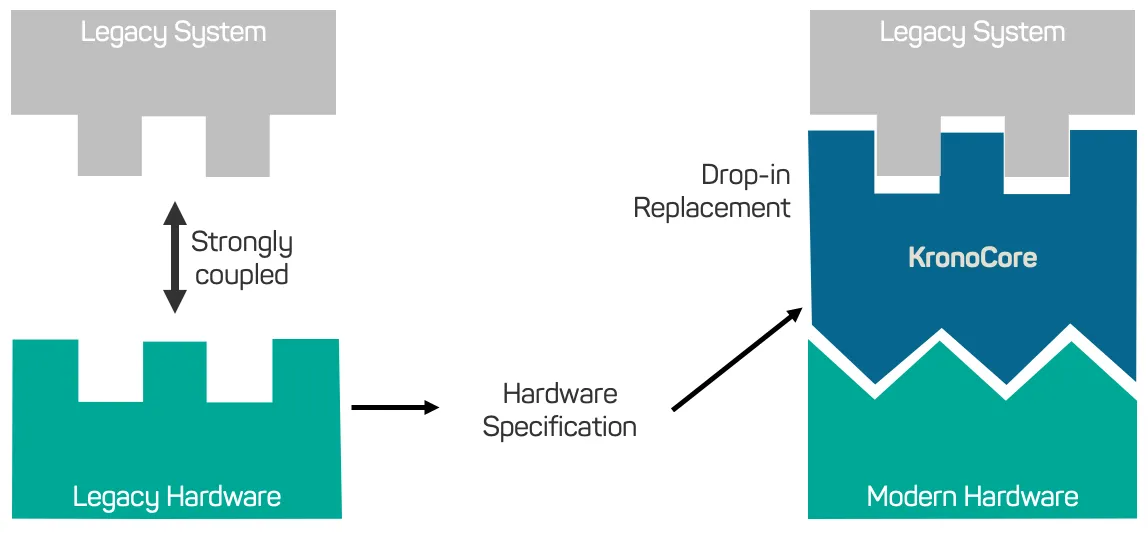
Fortunately, virtualization - the underlying technology of our lifetime extension solution KronoCore - can provide everything the old software expects on modern hardware. KronoCore is built with decades-long support in mind.
Cyber-Security is a challenge that needs to be looked at individually for each system. Virtualization allows us to encapsulate and isolate the legacy system and secure access to it. For example, if legacy software has known vulnerabilities, we can block access to these vulnerabilities and make sure the system stays secure. In essence this is an on-device firewall for the legacy system. What’s great about our approach is that we can provide these capabilities without changes to the existing software system.
Another challenge with legacy systems is that they often do lack modern cryptography, preventing secure remote access for operators. The existing crypto algorithms are often either broken completely or so weak that the effort to break them is negligible. With KronoCore we can provide secure access to these systems with modern cryptographic algorithms. KronoCore allows us to terminate the crypto on-device and keep the insecure communication off the network.
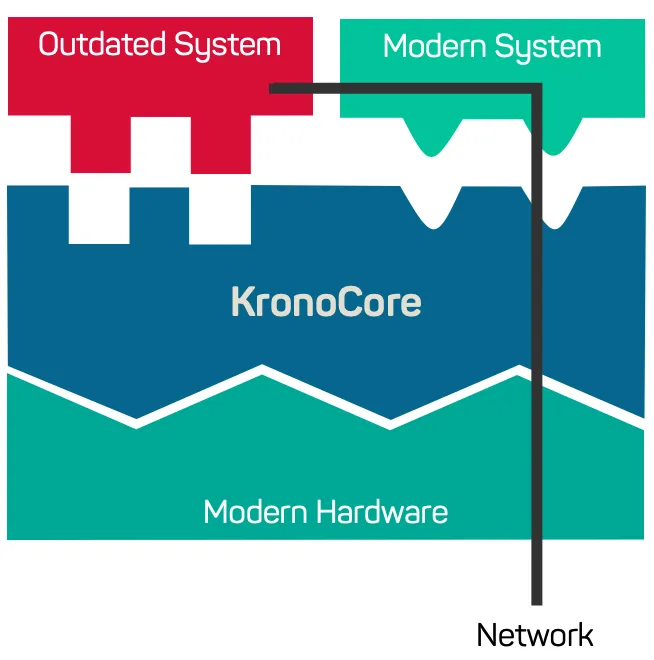
We can also use the same approach to help establish secure remote management channels for IT administrators, provide secure integration into the rest of the IT ecosystem or help with maintenance tasks, such as checking for failures. Because all access is terminated in a modern and supported system it is even possible to enable remote support or other remote access scenarios.
With KronoCore we are working to provide a solution that enables software lifetime to keep up with the planned lifetimes of physical infrastructure, by decoupling the stable, controlling portions of the software from the parts that interact with the ever-changing IT environment.
If these challenges sound familiar to you, or if you have unsupported systems that are critical for your business, we would love to hear from you. Reach out to us at service@cyberus-technology.de!